
A zero-day security flaw in Telegram’s Android mobile app, called EvilVideo, allowed attackers to access malicious files disguised as harmless-looking videos.
The exploit was put up for sale for an unknown price on an underground forum on June 6, 2024, ESET said. Following responsible disclosure on June 26, the issue was fixed by Telegram in version 10.14.5 released on July 11.
“Attackers could share malicious Android payloads via Telegram channels, groups, and chats, and make them appear as media files,” security researcher Lukáš Štefanko said in a report.
The payload is believed to have been crafted using Telegram’s application programming interface (API), which allows for the programmatic uploading of media files to chats and channels. In doing so, it allows an attacker to disguise a malicious APK file as a 30-second video.
Users who click on the video will see a warning message stating that the video cannot be played and prompting them to try playing it using an external player. If they continue with this step, they will then be asked to allow the APK file to be installed via Telegram. The app in question is called “xHamster Premium Mod.”
“By default, media files received via Telegram are set to be downloaded automatically,” Štefanko said. “This means that users who have enabled the option will automatically download the malicious payload once they open the conversation in which it was shared.”
While this option can be manually disabled, the payload can still be downloaded by pressing the download button accompanying the supposed video. It is worth noting that the attack does not work on Telegram clients for web or the dedicated Windows app.
It is not yet known who is behind this exploit or to what extent it has been used in real-world attacks. However, the same actor announced in January 2024 a completely undetectable Android encryptor (aka cryptor) that could bypass Google Play Protect.
Hamster Kombat’s Viral Success Spawns Malicious Copycat
The development comes as cybercriminals capitalize on the Telegram-based cryptocurrency game Hamster Kombat to make money, with ESET discovering fake app stores promoting the app, GitHub repositories hosting Lumma Stealer for Windows under the guise of automation tools for the game, and an unofficial Telegram channel used to distribute an Android trojan called Ratel.
The popular game, which is set to launch in March 2024, is said to have over 250 million players, according to the game’s developer. Telegram CEO Pavel Durov called Hamster Kombat “the fastest growing digital service in the world” and said that “the Hamster team will create its token on TON, introducing the benefits of blockchain to hundreds of millions of people.”
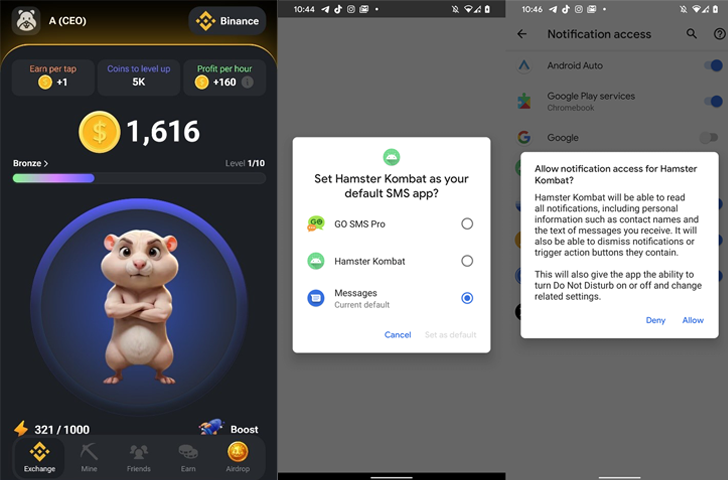
Ratel, offered via a Telegram channel called “hamster_easy,” is designed to mimic the game (“Hamster.apk”) and prompts users to grant it access to notifications and set itself as the default SMS app. It then initiates contact with a remote server to obtain a phone number in response.
In the next step, the malware sends an SMS in Russian to this phone number, probably belonging to the malware operators, to receive further instructions via SMS.
“The hackers can then control the compromised device via SMS: the message from the operator can contain a text to be sent to a specified number, or even ask the device to call that number,” ESET explains. “The malware is also able to check the current balance of the victim’s bank account with Sberbank Russia by sending a message containing the text баланс (translation: balance) to the number 900.”
Ratel is abusing its notification access rights to hide notifications from as many as 200 apps based on a hard-coded list embedded in the app. It is suspected that this is done in order to subscribe victims to various premium services and prevent them from being alerted.
The Slovakian cybersecurity firm said it has also spotted fake app stores that claim to offer Hamster Kombat for download but actually direct users to unwanted ads, as well as GitHub repositories offering Hamster Kombat automation tools that deploy Lumma Stealer instead.
“Hamster Kombat’s success has also attracted the attention of cybercriminals, who have already begun deploying malware targeting the game’s players,” said Štefanko and Peter Strýček. “Hamster Kombat’s popularity makes it ripe for abuse, meaning it is very likely that the game will attract more malicious actors in the future.”
BadPack malware on Android slips through the cracks
Beyond Telegram, malicious APK files targeting Android devices have also taken the form of BadPack, which refers to specially crafted package files in which the header information used in the ZIP archive format has been modified in an attempt to hamper static analysis.
By doing so, the idea is to prevent the AndroidManifest.xml file – a crucial file that provides essential information about the mobile application – from being extracted and properly parsed, thus allowing the installation of malicious artifacts without raising any red flags.
This technique was extensively documented by Kaspersky in early April in connection with an Android Trojan called SoumniBot that targeted users in South Korea. Telemetry data collected by Palo Alto Networks Unit 42 from June 2023 to June 2024 detected nearly 9,200 BadPack samples in the wild, though none of them were found on the Google Play Store.
“These forged headers are a key feature of BadPack, and such samples typically pose a challenge to Android reverse engineering tools,” said Lee Wei Yeong, a researcher at Unit 42, in a report published last week. “Many Android-based banking Trojans like BianLian, Cerberus, and TeaBot use BadPack.”