What is malware?
Kurt “CyberGuy” Knutsson explains how to protect yourself against malware and ransomware.
Online protection company Proofpoint warns that sophisticated new malware that impersonates Google Chrome and Microsoft has the potential to steal money from Windows device owners. Several groups of cybercriminals use this malware, some of which are known to send spam emails that can infect computers with malware Or Ransomware.
The malware presents itself as fake updates in Internet browsers like Chrome to trick users into downloading harmful code. Once the code is on the computer, hackers can access cryptocurrencies, sensitive files and personal information.
GET SECURITY ALERTS, EXPERT TIPS – SUBSCRIBE TO KURT’S NEWSLETTER – THE CYBERGUY REPORT HERE

Microsoft Laptops (Microsoft) (Kurt “CyberGuy” Knutsson)
How Does Fake Update Malware Work?
Point of proof identified wider distribution of the malware this month, but the online protection company estimates the campaign has been running since March 2024. The malware masquerades as fake Google Chrome, Word and OneDrive errors to coerce users to download harmful code. These errors prompt the visitor to click a button to copy a PowerShell “fix” to the clipboard, then paste and run it in a Run dialog box or PowerShell prompt.
“While the attack chain requires significant user interaction to be successful, social engineering is smart enough to present to someone what looks like a real problem and a solution simultaneously, which can prompt a user to act without considering the risk,” warns Proofpoint.
When the PowerShell script runs, it checks if the device is a valid target. Then it downloads more payloads. These steps include clearing the DNS cache, deleting clipboard contents, displaying a fake message, and downloading another remote PowerShell script.
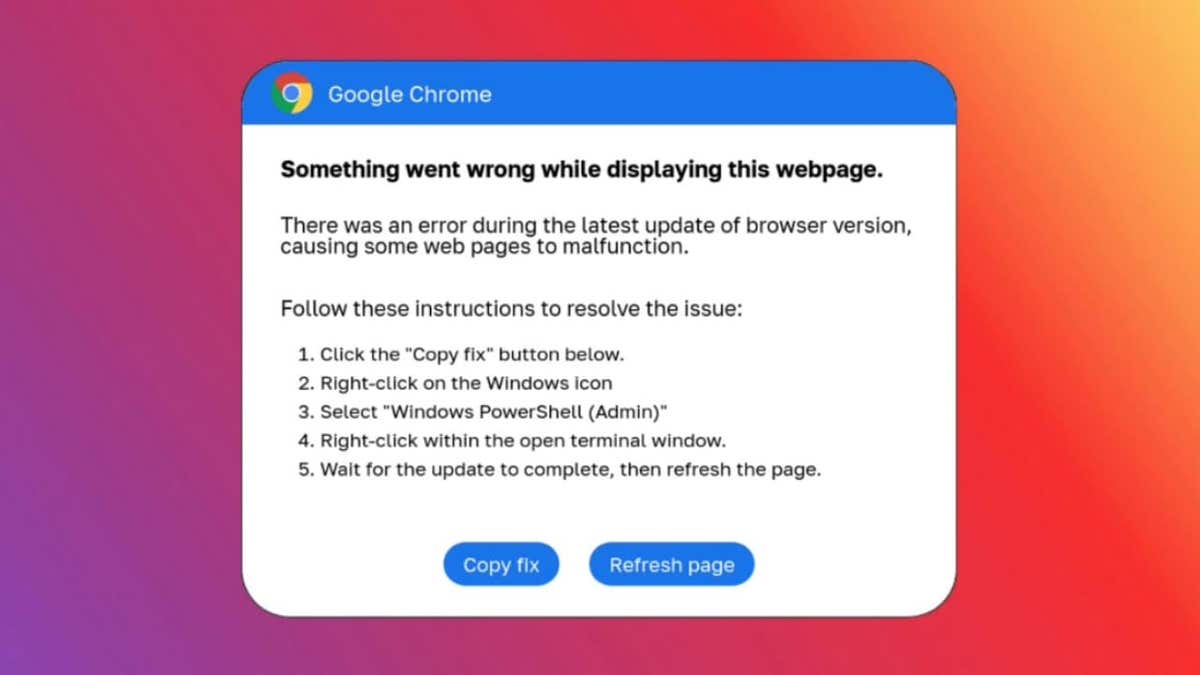
ClickFix error message (Proofpoint) (Kurt “CyberGuy” Knutsson)
BEST ANTIVIRUS FOR PC, MACS, IPHONES AND ANDROIDS – CYBERGUY PICKS
Cryptocurrency theft
This second script checks if it is running on a virtual machine before downloading an information stealer. Once everything is ready, the hacker can access the victim’s cryptocurrency. This system redirects the victim’s funds to the hacker rather than the intended recipient.
Alternative attack method: Email luring
Proofpoint notes that bad actors also use another method called “email luring” to install harmful software. Emails, usually those that appear work or business related, contain an HTML file that looks like Microsoft Word. These emails prompt users to install the “Word Online” extension to view the document correctly.
Similar to the method above, users are prompted to open PowerShell and copy the malicious code. Proofpoint claims the misleading “campaign” is widespread. “The campaign included more than 100,000 messages and targeted thousands of organizations around the world,” according to the company.
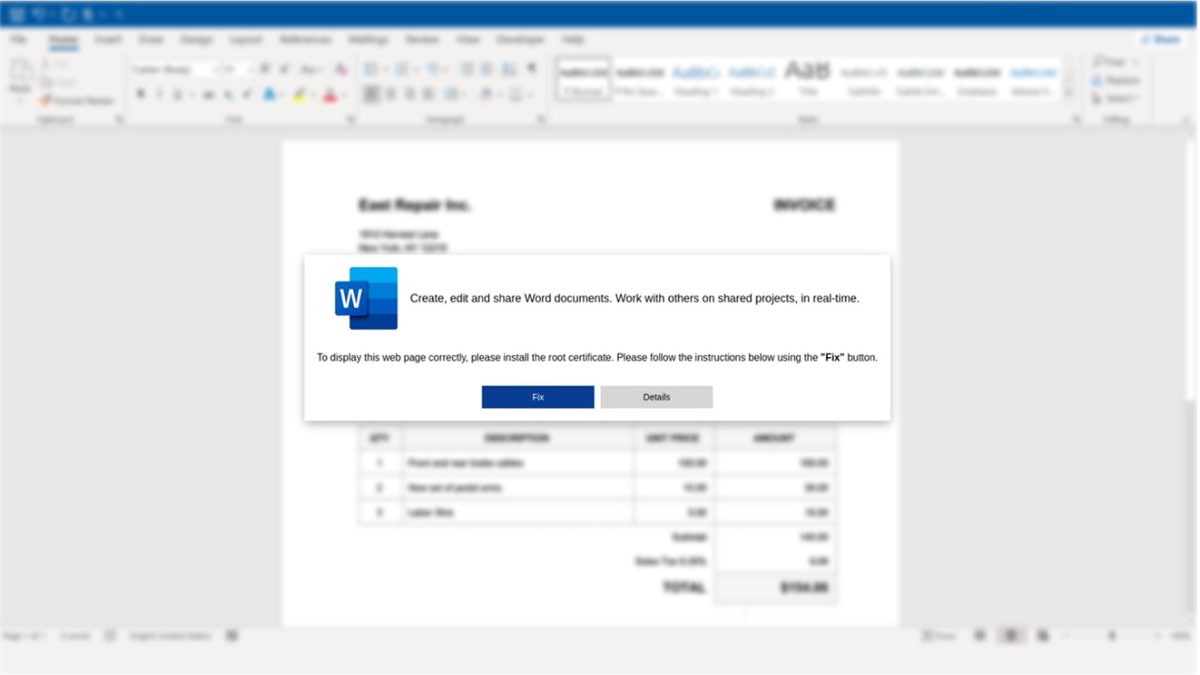
HTML attachment containing instructions on how to copy and paste PowerShell that leads to malware installation (Proofpoint) (Kurt “CyberGuy” Knutsson)
DON’T LET NEARBY SNOOPS LISTEN TO YOUR VOICE MESSAGE WITH THIS QUICK TIP
5 ways to protect yourself from harmful software
Fake Chrome and Microsoft Word malware create a sense of urgency, tricking users into clicking links and unknowingly compromising their devices. There are several steps you can take to protect yourself against this malware.
1) Have powerful antivirus software: The best way to protect yourself from malicious links that install malware that can access your private information is to install antivirus protection on all your devices. This can also alert you to any phishing emails or ransomware scams. Get my picks for the best 2024 antivirus protection winners for your Windows, Mac, Android and iOS devices.
2) Use a VPN: Consider using a VPN to protect against tracking and to identify your potential location on websites you visit. Many sites can read your IP address and, depending on their privacy settings, display the city you correspond from. A VPN will hide your IP address to show another location. For the best VPN software, check out my expert review of the best VPNs for browsing the web privately on your computer. Windows, Mac, Android and iOS devices.
3) Monitor your accounts: Regularly review your bank statements, credit card statements and other financial accounts for unauthorized activity. If you notice any suspicious transactions, report them immediately to your bank or credit card company.
4) Place a fraud alert: Contact one of the three major credit reporting agencies (Equifax, Experian, or TransUnion) and request that a fraud alert be placed on your credit report. This will make it more difficult for identity thieves to open new accounts in your name without verification.
5) Enable two-factor authentication: Enable two-factor authentication as soon as possible. This adds an extra layer of security by requiring a second form of verification, such as a code sent to your phone, in addition to your password.
HOW TO DELETE YOUR PRIVATE DATA FROM THE INTERNET
Kurt’s Key Takeaways
Hackers have cleverly designed malware that invites you to install it on your devices. This malware specifically targets Windows users, and I’ve noticed that Windows devices seem more susceptible to these types of attacks. Recently, Microsoft admitted a Wi-Fi driver flaw in Windows that allows hackers to hijack your PC simply by being on the same Wi-Fi network. It is essential to be careful when browsing online or connecting to a public Wi-Fi network.
How to verify the authenticity of software before downloading and installing it on your device? Let us know by writing to us at Cyberguy.com/Contact.
For more of my tech tips and security alerts, subscribe to my free CyberGuy Report newsletter by visiting Cyberguy.com/Newsletter.
Ask Kurt a question or tell us what stories you’d like us to cover.
Follow Kurt on his social media
Answers to the most asked CyberGuy questions:
Copyright 2024 CyberGuy.com. All rights reserved.